EMPOWERING YOUR DIGITAL FURTURE
Secure your infrastructure 24/7—with minimal effort for your team
This page provides an overview of our services relating to
secure networks, monitoring & Network Operations Center (NOC),
Managed services and attack detection systems (SzA) in accordance with BSI specifications.
Our focus: Critical infrastructures & secure networks
Whether you are a KRITIS operator, mechanical engineering company, medium-sized business, or enterprise:
We are your partner when availability, security, and transparency in the network are business-critical.
Our core customers are primarily critical businesses, e.g.:
- Electricity and gas providers
- Telecommunications company
- Healthcare facilities (especially hospitals)
In addition, we serve numerous medium-sized customers, for example in mechanical and plant engineering, manufacturing, and service companies, whose networks have similar requirements in terms of availability, segmentation, and security.
In short: wherever a network “must always be up and running” and sensitive data must be protected at the same time, we feel right at home.
When designing networks, we follow the guidelines of the BSI (German Federal Office for Information Security) – in particular the ISi-LANA guideline “Secure connection of local networks to the Internet”. This provides clear recommendations on how local networks should be structured and securely connected to the Internet via a security gateway (packet filter + application gateway):

Important principles that we consistently implement from these guidelines:
-
No direct routing
- from the Internet to the local network – Every connection runs through defined security zones and gateways. -
Strict service separation
- Critical services are separated logically and physically, e.g., separation of management, server, user, and DMZ networks. -
Vendor break
– We deliberately use different manufacturers in critical chains (e.g., Internet firewall from manufacturer A, internal segment from manufacturer B) to avoid common vulnerabilities and single points of failure. -
Logging and monitoring as a requirement, not an option
– All security-related components are centrally monitored and evaluated.
At the same time, we help our customers to more easily meet ISO 27001 requirements and BSI specifications—especially in the context of KRITIS and IT Security Act 2.0.
How we build infrastructure
P-A-P security concept – explained as at the airport
How we build infrastructure
P-A-P security concept – explained as at the airport
Our security concept typically follows a P-A-P approach:
Portfilter – Application Layer Gateway – Portfilter
Instead of explaining it in highly technical terms, we like to use the airport example:
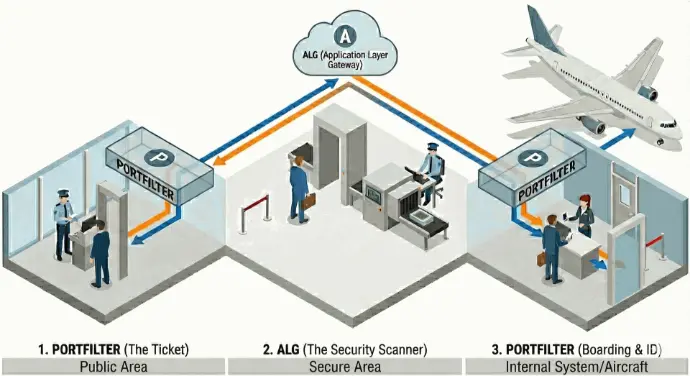
- First port filter = Your flight ticket at the airport entrance
- Without a ticket, you won't even be allowed into the airport area.
- Applied to IT: The first packet filter (firewall) decides which connections from outside are allowed to pass through to the security zone.
-
Application Layer Gateway = Security check with scanner
- Here you go through the scanner, your luggage is X-rayed, and prohibited items are sorted out.
- Applied to IT: The application layer gateway checks the actual content of the connection (e.g., HTTP, DNS, mail) and only lets through what is really allowed and clean.
-
Second port filter = ticket + ID when boarding the aircraft
- Before you board the plane, your ticket and ID will be checked again.
- Applied to IT: An additional packet filter protects the internal network and ensures that only defined, verified connections reach the target system.
Benefits for managers clearly summarized:
- Multi-layered protection instead of “one big firewall and you're done”
- Better controllable risks through clear zones and roles
-
Implementable in accordance with BSI guidelines (ISi-LANA), i.e., audit-proof for audits and certifications
Monitoring & Network Operations Center (NOC)
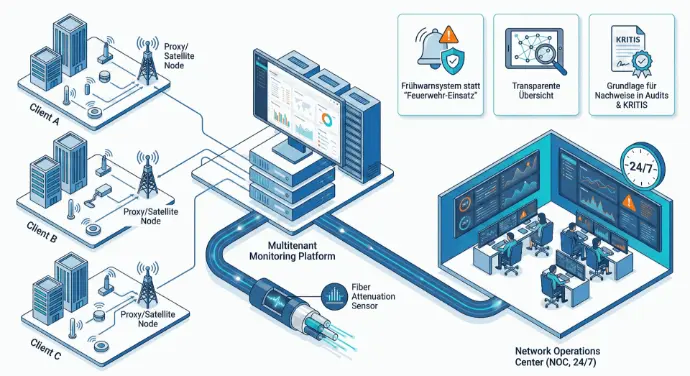
In parallel with our managed services business, we have developed a highly advanced monitoring system:
- Multi-tenant-enabled monitoring platform
- Use of proxy/satellite nodes at the customer's site
- Recording of a wide variety of sensor data – including fiber optic attenuation
- Close integration with our Network Operations Center (NOC, 24/7)
Benefits for you:
- Early warning system instead of “firefighting”
- Transparent overview of the status of your networks and systems
- Basis for evidence in audits and KRITIS inspections
On-call service & alarm management
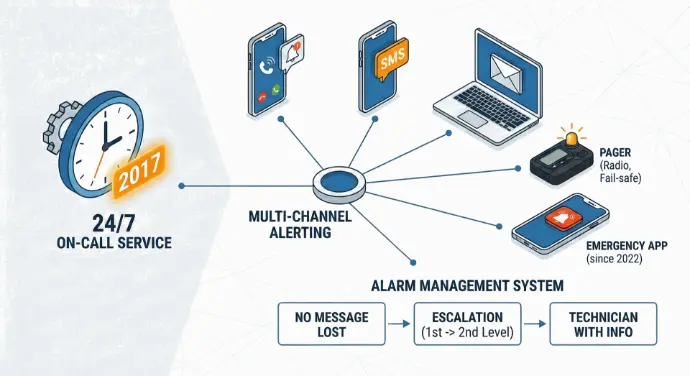
We introduced a structured on-call service back in 2017 so that we can respond quickly even outside of business hours.
Our alarm concept includes:
-
Multi-channel alert
- Mobile communications (call/push)
- SMS
- Pager (radio pager)
- Since 2022, an additional emergency app for smartphones
What is a pager?
A pager is a small, robust radio receiver that receives short messages or alarm codes – independently of smartphone apps. It is typically used in control centers, clinics, and fire departments because it is very fail-safe and continues to function even when other channels are disrupted.
Using a sophisticated alarm management system, we ensure that:
- No notification gets lost,
- Escalations run automatically (e.g., 1st level → 2nd level),
- The right technician is provided with all the necessary information as quickly as possible.
Managed Services
Since 2018, we have focused clearly on:
- Managed Network Services
- Security solutions based on the P-A-P principle
-
Operation of these solutions in accordance with BSI guidelines (including ISi-LANA)
This includes product design that is geared toward meeting the requirements for attack detection systems (SzA) in accordance with § 8a (1a) BSIG—and to a high degree of implementation (level 5) —while keeping financial costs for our customers deliberately low.
In short:
We combine network operations (NOC) and security monitoring (SOC) into a coherent package that is specifically designed to meet the regulatory requirements of KRITIS companies.
Central Operations Dashboard (COD) von extocode
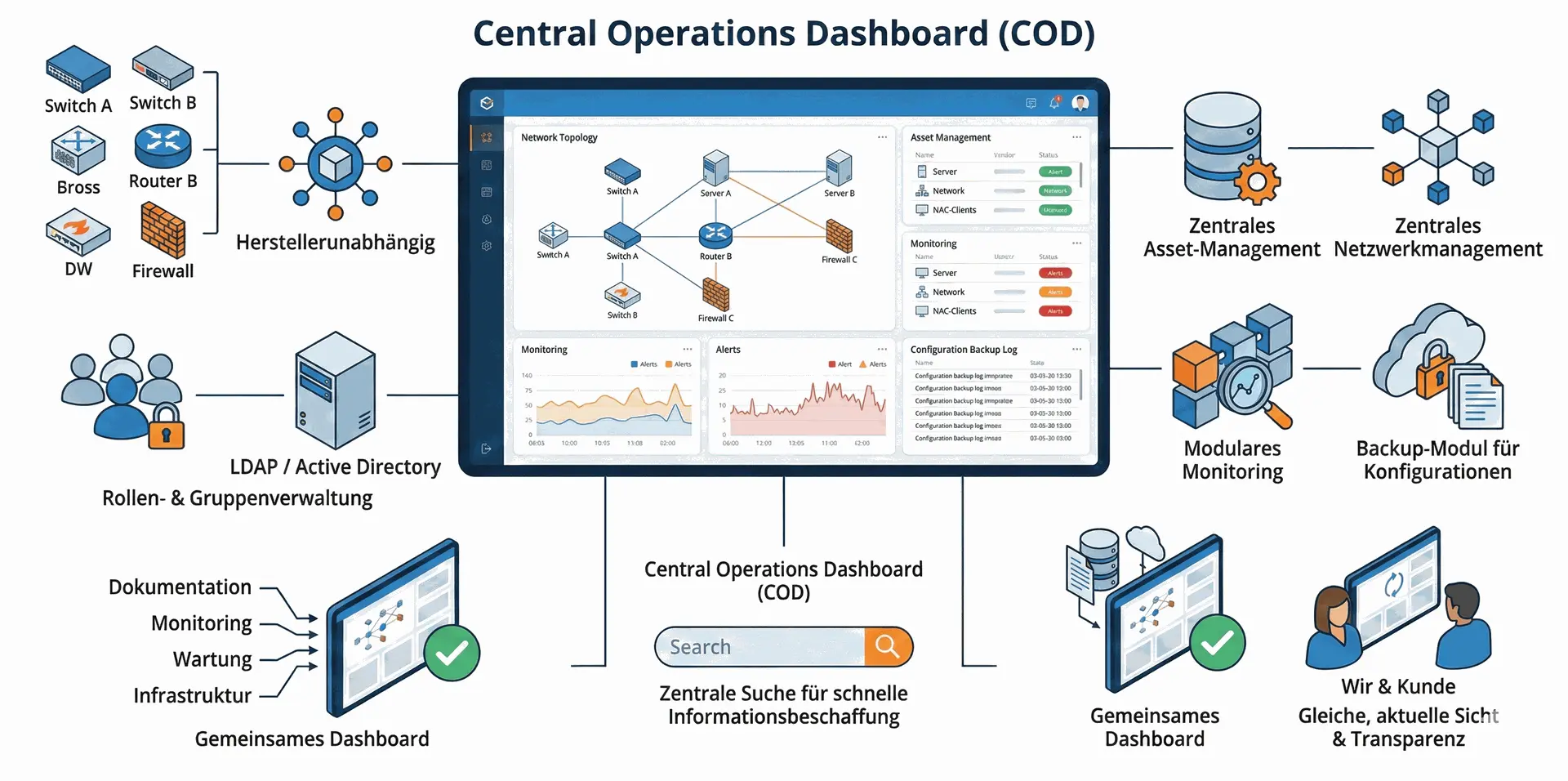
To manage the large number of manufacturers (switches, routers, firewalls, etc.) effectively, we use the Central Operations Dashboard (COD) from extocode GmbH:
👉 Central Operations Dashboard (COD) form extocode GmbH
What makes COD special?
- Central platform for a wide variety of infrastructure systems from differentmanufacturers
- Manufacturer-independent – ideal for environments with multiple vendors
- Multi-tenant capable
- Role & group management, including connection to external LDAP / ActiveDirectory
- Central asset management (servers, network, NAC clients, etc.)
- Central network management with overview of topology and details
- Modular monitoring – integrated into your existing monitoring system
- Backup module for configurations (e.g., firewalls, switches, Linux/BSD systems)
- Central search for fast information retrieval, e.g.,for first-level support
For our customers, this means:
- Documentation systems, monitoring, maintenance calendars, and infrastructure data are consolidated in a shared dashboard
- We and the customer see the same, up-to-date view of the infrastructure—ideal for transparency, operations, audits, and collaboration.
Get in touch with us today!
for your individual consultation!